
YOU
CAN'T
HACK
biometrics
When it comes to protecting your internet business, You don't want to be on
the ignorance is bliss only to Find Out The Hard Way Side
Grab The "Am I CyberSafe in the digital space?"
Phone App CyberSecurity Guide
And You Won't Have To...
When it comes to protecting your internet business, You don't want to be on
the ignorance is bliss only to Find Out The Hard Way Side
Register for The "Securista CyberSquad Workshops" Today
And You Won't Have To...
FROM THE CYBERSECURITY EXPERT WHO FOUND
THE 1ST SOCIAL MEDIA MALWARE
Layered

Home

Phone

Business
defense
As An Internet User, Protecting Everything, Especially Your devices, platforms, and personal information, is critical.
let's Protect your digital life
Your Data Is Your's
Text Message Opt-in

Here's a peek at What I Know
The Lockdown

iPhone’s Stolen Device Protection
UPDATE YOUR iPHONE
If you haven’t updated to the latest Apple iOS 17.3.
Why? Apple has added a new tool to iOS 17.3.
Stolen Device Protection

Let’s go over how to turn on the iPhone’s Stolen Device Protection tool.
You’ll need to:
Make sure your iPhone is updated to iOS 17.3.
Open the Settings app,
Scroll to Face ID & Passcode,
Then to Stolen Device Protection, and
Turn the switch on.
It’s that simple. One small toggle in your phone’s settings, but once turned on Stolen Device Protection puts extra limits on some settings..
Let’s go over why you’d really want to do this.
What that means for you is if someone unlocks your phone and tries to change the Stolen Device Protection settings, they’ll have to use Face ID or Touch ID.
Let’s say a thief has your phone and passcode, they won’t be able to change certain settings unless they have your biometric information too, after all you are difficult to clone.
Here’s the settings scoop. Those biometric security layers come into play when someone tries to access:
The passwords or passkeys (this is what you should already be using) you’ve saved in iCloud’s keychain,
Use payment methods saved in Safari,
Turn off Lost Mode,
Erase your phone,
Use your phone in the setup of a new Apple device,
Apply for a new Apple Card,
View your Apple Card’s virtual number (the best security for privacy and protection when shopping online), or
Transfer money with Apple Cash.
I’m sure you’re going to love the deeper security layer for the most sensitive information and yes, I made my Hubs add this on his iPhone.
Now, say you’re out and about, if your phone is not at a familiar location, like home or work, a one-hour “security delay” is turned on after using your biometrics. When this one-hour delay is up, your biometrics are needed again to change the settings.
Oh and your iPhone is totally accessible during this hour.
Why it matters: This security layer helps delay a thief from quickly taking over your phone or accounts by making changes, like:
Attempts to change your Apple ID password,
Sign out of Apple ID, or
Update Apple ID account security settings, such as removing a trusted device.
Remove Face ID or Touch ID accounts,
Change your iPhone passcode,
Reset your settings,
Disable the Find My tool, and
Turn off Stolen Device Protection itself.
Drop a comment below when you’ve secured your iPhone.
Here's a peek at What I'm Up To
online DefendHer
01
GhostMode Cybersecurity workshops, Trainings, & Security Updates
I've got workshops and understanding cybersecurity trainings in the works. But if you need help you can book a security call. We'll cover protection and defense... securing your home networks and more. Then we'll tackle how to shield your privacy... out in the wild. Finally, learn the favorite techniques and products security experts use to shut down access to those all important social apps.
02
GhostMode Cybersecurity Trainings
I created the GhostMode Cybersecurity 101 & 201 Series to bring cutting edge, up-to-date security info and how to understand it. We'll cover AI, Web3, and even blockchain technologies in easy to understand every day language.
03
Consulting: security strategy & Security updates
We call the vulnerable point of attack an endpoint. We can start with a security audit and create a strategy of recommended products and services you can tailor to your home or business needs. You'll have access to recurring security updates and previews of what we're seeing in the cyberworld.
If I like you, I'll tell you about the Billion $ heist
Meet Your Security Expert
Oh Hello! I’m Angela "Ange Gos" Payton. I've reverse-engineered malware and as the tech copywriter, I made tech jargon understandable for everyday people. Retiring from the Security and Response team at Symantec didn't end my cybersecurity life.
My corporate copywriting clients, top competitors of my former company, wanted less technobabble in their marketing info, anchoring and keeping me deep in cybersecurity for years.
After several years of copywriting for competitors, why pivot to cybersecurity, now? I watched a "cybersecurity expert" with zero threat experience provide outdated information... so outdated, I knew I needed to help internet denizens, like yesterday because I have a wealth of knowledge and How-To's people need.
So here we are.

I live in a California Wine Country. It's a good Life!
Ready to Give A Phisher The Phinger?
Imagine keeping your family, home, AND business safe. Simply and easily.
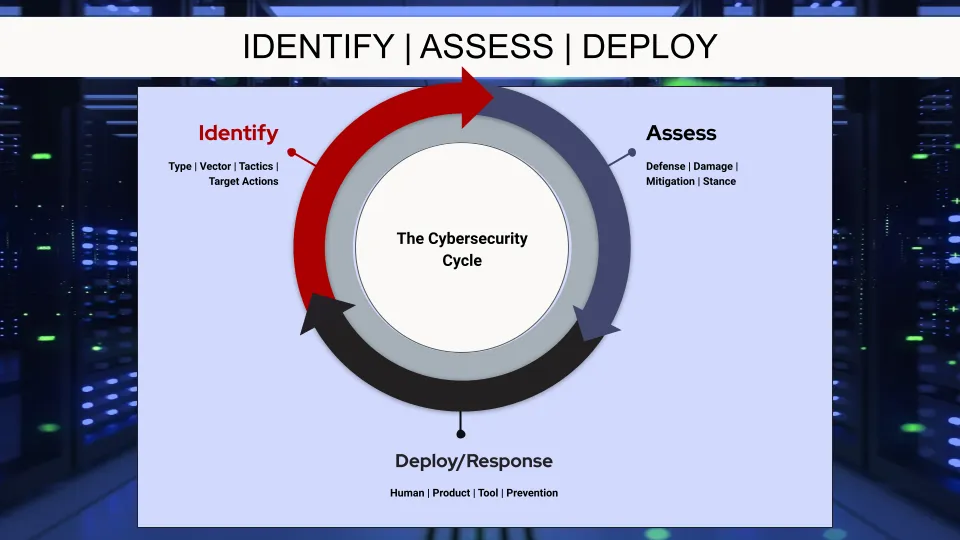
What We Do...

what Others are saying...
“A really strong testimonial that confirms the transformation that is waiting.”
Lorem ipsum dolor sit amet, consectetur adipisicing elit. Autem dolore, alias, numquam enim ab voluptate id quam harum ducimus cupiditate similique quisquam et deserunt, recusandae. Lorem ipsum dolor sit amet, consectetur adipisicing elit. Autem dolore, alias, numquam.
Jane Awesome, ABC Co.
THE VALUE DOESN'T STOP THERE You'll Also Get These Benefits...
01
Guest speakers/trainers
Get To Know Some Seriously Smart People
I haz friends. I've already started inviting experts to come and talk about security trends and what's next. There may even be some history stories about how some threats were found.

02
The categorical list o'things
Apps, Tools, & SaaS Worth Considering
In the member's area, we'll have a dedicated set of lists for apps, tools, & SaaS (both Software as a Service and Security as a Service). We'll cover who's behind them and what they cover.

03
of course!
Security Isn't Sexy Until It Saves Your Ass
An ounce of prevention... yada, yada. But really, think of how cool it will feel to know the latest social phishing scams and shutting it down. That's where our courses come in. Based on the Categorical Lists O'Security, we break down the how so you can decide if it'll work great for your or keep your $$. We'll also offer courses that will the protection protocols you'll use often.

