
YOU
CAN'T
HACK
biometrics
When it comes to protecting your internet business, You don't want to be on
the ignorance is bliss only to Find Out The Hard Way Side
Grab The "Am I CyberSafe in the digital space?"
Phone App CyberSecurity Guide
And You Won't Have To...
When it comes to protecting your internet business, You don't want to be on
the ignorance is bliss only to Find Out The Hard Way Side
Register for The "Securista CyberSquad Workshops" Today
And You Won't Have To...
FROM THE CYBERSECURITY EXPERT WHO FOUND
THE 1ST SOCIAL MEDIA MALWARE
Layered

Home

Phone

Business
defense
As An Internet User, Protecting Everything, Especially Your devices, platforms, and personal information, is critical.
let's Protect your digital life
Your Data Is Your's
Text Message Opt-in

Here's a peek at What I Know
The Lockdown

Threat Alert CVE-2023-44487 HTTP/2 RAPID RESET
UPDATE 11/17/2023
Patching continues.
THREAT ALERT: CVE-2023-44487 “HTTP/2 RAPID RESET”
Published: 2023-10-10 Updated: 2023-10-16
Base Score: 7.5 HIGH Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H

ATTACK TYPE
DDoS (Dedicated Denial of Service) attacks
A DDoS occurs when attackers attempt to overwhelm a service with junk traffic. The goal is to bring the service down.
An attack doesn't need to be fancy to be a pain in the butt, the ability to access any digital service, from critical infrastructure to crucial information is vital for all organizations.
These attacks are a classic internet menace and will continue to as hackers are always working on new strategies in an effort to make a DDoS bigger or more effective.
SUMMARY
GOOGLE, AMAZON, MICROSOFT, and Cloudflare revealed this week that they battled massive, record-setting distributed denial of service attacks against their cloud infrastructure in August and September that used CVE-2023-44487.
The HTTP/2 protocol allows a denial of service (server resource consumption) because request cancellation can reset many streams quickly, as exploited in the wild in August through October 2023.
An important point to note is where the vulnerability came from. Rapid Reset is not a particular piece of software. It’s in the specification for the HTTP/2 network protocol used for loading webpages. Developed by the Internet Engineering Task Force (IETF), HTTP/2 is the faster and more efficient version of the classic internet protocol HTTP and has been the standard for about eight years. HTTP/2 has been widely adopted as it works better on mobile and uses less bandwidth. IETF is currently developing HTTP/3.
This exploit is rare as a vulnerability in a standard is unusual. Lucky for us, by carrying out the assaults, hackers revealed the existence of the protocol vulnerability and how it could be exploited. We call that cause and effect “burning a zero day.”
So you know, unlike a specific software exploit, like, a Windows bug that gets patched by Microsoft or a Safari bug that gets patched by Apple, a flaw in a protocol can't be fixed by one central entity because each website implements the standard in its own way. Sounds bad, right?
But it’s not, with one exception. When major cloud services and DDoS-defense providers create fixes for their services, it goes a long way toward protecting everyone who uses their infrastructure. The exception? Organizations and individuals running their own web servers need to work out their own protections.
THE BAD NEWS
DDoS attacks can have wide-ranging consequences, including loss of business and unavailability of critical applications. Recovery and remediation can go far beyond the end of an attack
The recent attacks were particularly noteworthy, though, because hackers generated them by exploiting a vulnerability in a foundational web protocol. This means that while patching efforts are well underway, fixes will need to essentially reach every web server globally before these attacks can be fully stamped out.
This attack abuses an underlying weakness in the HTTP/2 protocol and any vendor that has implemented HTTP/2 will be subject to the attack.” What this means is the problem is generally relevant to every modern web server.
It will take years to reach full adoption of these patches, though, and there will still be some services that did their own HTTP/2 implementation from scratch and don't have a patch coming from anywhere else.
The scary thing is that the big tech companies discovered this while it was being actively exploited and that means it can be used to take a service down like operational tech or industrial control which would impact infrastructures, including publicly relied upon governmental ones.
THE GOOD NEWS
Dubbed “HTTP/2 Rapid Reset,” the vulnerability can only be exploited for denial of service—it doesn't allow attackers to remotely take over a server or exfiltrate data.
One great thing to note in this situation is that the availability of open source and the prevalence of code reuse (instead of always building everything from scratch) is a big advantage. Most likely, many web servers have copied their HTTP/2 implementation from somewhere else rather than reinvent the wheel and if these projects are maintained, they will develop Rapid Reset fixes that can proliferate out to users.
Though the string of recent DDoS attacks on Google, Cloudflare, Microsoft, and Amazon raised the alarm for being so large, the companies were ultimately able to repel the attacks, which didn't cause lasting damage.
Even though the patching process will take time, and some web servers will remain vulnerable long term, the internet is safer now than if attackers hadn't shown their cards by exploiting the flaw.
Here's a peek at What I'm Up To
online DefendHer
01
GhostMode Cybersecurity workshops, Trainings, & Security Updates
I've got workshops and understanding cybersecurity trainings in the works. But if you need help you can book a security call. We'll cover protection and defense... securing your home networks and more. Then we'll tackle how to shield your privacy... out in the wild. Finally, learn the favorite techniques and products security experts use to shut down access to those all important social apps.
02
GhostMode Cybersecurity Trainings
I created the GhostMode Cybersecurity 101 & 201 Series to bring cutting edge, up-to-date security info and how to understand it. We'll cover AI, Web3, and even blockchain technologies in easy to understand every day language.
03
Consulting: security strategy & Security updates
We call the vulnerable point of attack an endpoint. We can start with a security audit and create a strategy of recommended products and services you can tailor to your home or business needs. You'll have access to recurring security updates and previews of what we're seeing in the cyberworld.
If I like you, I'll tell you about the Billion $ heist
Meet Your Security Expert
Oh Hello! I’m Angela "Ange Gos" Payton. I've reverse-engineered malware and as the tech copywriter, I made tech jargon understandable for everyday people. Retiring from the Security and Response team at Symantec didn't end my cybersecurity life.
My corporate copywriting clients, top competitors of my former company, wanted less technobabble in their marketing info, anchoring and keeping me deep in cybersecurity for years.
After several years of copywriting for competitors, why pivot to cybersecurity, now? I watched a "cybersecurity expert" with zero threat experience provide outdated information... so outdated, I knew I needed to help internet denizens, like yesterday because I have a wealth of knowledge and How-To's people need.
So here we are.

I live in a California Wine Country. It's a good Life!
Ready to Give A Phisher The Phinger?
Imagine keeping your family, home, AND business safe. Simply and easily.
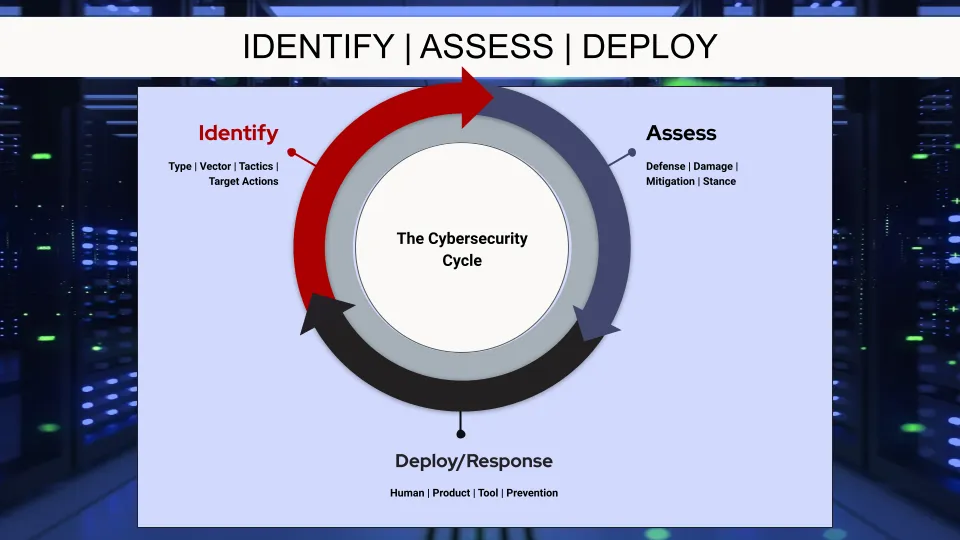
What We Do...

what Others are saying...
“A really strong testimonial that confirms the transformation that is waiting.”
Lorem ipsum dolor sit amet, consectetur adipisicing elit. Autem dolore, alias, numquam enim ab voluptate id quam harum ducimus cupiditate similique quisquam et deserunt, recusandae. Lorem ipsum dolor sit amet, consectetur adipisicing elit. Autem dolore, alias, numquam.
Jane Awesome, ABC Co.
THE VALUE DOESN'T STOP THERE You'll Also Get These Benefits...
01
Guest speakers/trainers
Get To Know Some Seriously Smart People
I haz friends. I've already started inviting experts to come and talk about security trends and what's next. There may even be some history stories about how some threats were found.

02
The categorical list o'things
Apps, Tools, & SaaS Worth Considering
In the member's area, we'll have a dedicated set of lists for apps, tools, & SaaS (both Software as a Service and Security as a Service). We'll cover who's behind them and what they cover.

03
of course!
Security Isn't Sexy Until It Saves Your Ass
An ounce of prevention... yada, yada. But really, think of how cool it will feel to know the latest social phishing scams and shutting it down. That's where our courses come in. Based on the Categorical Lists O'Security, we break down the how so you can decide if it'll work great for your or keep your $$. We'll also offer courses that will the protection protocols you'll use often.

